Is Quantum Computing the End of Blockchain’s Cryptography?
Today, blockchain technology rests on cryptographic foundations designed for classical computers. As the landscape of computing evolves, however, a powerful new player — Quantum Computing — is moving center-stage. This has profound implications for blockchains, which rely on cryptographic algorithms assumed to be infeasible to classical attacks. In 2025, the question is when and how networks must transition. This article explores the current state of quantum computing, the threats it poses to blockchain, how networks are preparing, and what builders and users should do now.
What Is Quantum Computing?
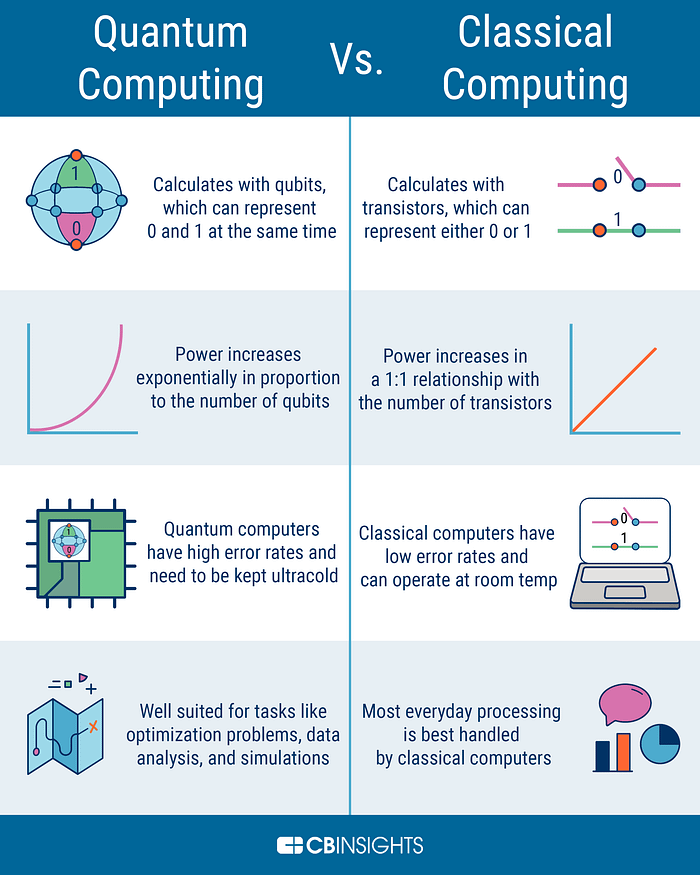
Quantum computing is an emergent field of computer science and engineering that leverages quantum mechanics — the laws that govern particles at atomic and sub-atomic scales — to process information in fundamentally new ways.
Core Concepts
- Qubits vs Classical Bits
Unlike a classical bit, which holds a single state (either 0 or 1), a quantum bit (qubit) can exist in a superposition of both states simultaneously (i.e., 0 and 1). This property allows quantum systems to represent and manipulate a vastly larger space of possibilities. - Entanglement
When qubits become entangled, the state of one can instantly correlate with the state of another, regardless of distance. This enables coordinated information that classical bits cannot replicate. - Quantum Interference & Measurement
Quantum algorithms exploit interference effects to amplify correct outcomes and suppress incorrect ones. Once you measure a qubit, its superposition collapses to a definite state — making the timing and structure of operations vital.
Why Quantum Computers Matter
Quantum computing promises to solve particular classes of problems exponentially faster than classical computers can. Examples include factoring large integers, searching unsorted data, simulating quantum systems, and optimizing complex combinatorial problems. At the same time, current quantum hardware is still in the Noisy Intermediate-Scale Quantum (NISQ) era — devices with dozens to thousands of qubits that are prone to errors and not yet fault-tolerant.
The State of Quantum Computing in 2025
Quantum computing has made notable progress, though it has not yet reached the threshold for widespread disruption of blockchain.
- Google’s Willow chip (105 physical qubits) and similar processors from IBM demonstrate quantum advantage in narrow problems — but cannot yet break RSA or ECC at scale.
- Forecasts for when quantum computers become “cryptographically relevant” for blockchain range from 2026–2035, depending on progress in error correction, qubit scalability, and algorithmic refinements.
So while quantum computing remains an emerging threat, it is increasingly considered plausible and urgent rather than purely theoretical.
Why Blockchains Are at Risk
Blockchain networks rely on several cryptographic primitives — primarily public-key signature schemes (e.g., ECDSA) and hash functions (e.g., SHA-256) — that quantum computers can compromise via algorithms like Shor’s Algorithm and Grover’s Algorithm.
- With Shor’s algorithm, a sufficiently powerful quantum machine could derive a private key from a known public key — exposing funds in wallets and undermining signature-based trust.
- Grover’s algorithm offers quadratic speed-ups in hash-function inversion, enabling faster collision-search or nonce-finding attacks under specific consensus models.
- A detailed threat analysis warned that billions of dollars of crypto assets remain vulnerable, especially funds sitting in addresses that have already revealed their public keys or re-used addresses. okx.com+1
- Consensus-layer risks: In theory, if hashing or signature security collapses, attackers could manipulate block production, execute 51 % attacks, or rewrite ledger history.
In short, the cryptographic infrastructure underlying blockchain is highly exposed if quantum computing scales significantly.
Key Threat Vectors
Here are the main attack surfaces relevant to blockchain networks in a quantum scenario:
- Key Exposure (Wallets)
Addresses that already reveal public keys are especially vulnerable. A quantum attacker may “harvest now, decrypt later” — collect public keys today and break them when quantum capability emerges. - Signature Forgery & Transaction Manipulation
If an attacker can derive private keys, they could forge transactions, move funds, or change state immutably. This undermines the trust model of blockchains. - Consensus & Chain Integrity
Advanced quantum attacks could enable chain reorganizations or block substitutions, especially if hashing becomes insecure. While this remains more speculative, some studies warn of the risk. - Transition Period Risks
Even before full quantum capability arrives, attackers could stash encrypted data or tokens for future decryption (“store now, decrypt later”), creating latent risk.
How the Blockchain Community Is Responding
Several initiatives are underway to mitigate the quantum threat and steer blockchain networks into a “quantum-safe” future:
- Post-Quantum Cryptography (PQC): Many academics and standards bodies (such as the National Institute of Standards and Technology, NIST) are standardizing quantum-resistant algorithms like CRYSTALS-Dilithium, Falcon, SPHINCS+, and lattice-based schemes.
- Quantum-Safe Frameworks for Blockchain: Projects like Quantum Resistant Ledger (QRL) are built from the ground up using hash-based signatures (XMSS) to be quantum-resistant.
- Migration Planning: Several financial-sector bodies (e.g., Europol-led Quantum Safe Financial Forum) are urging institutions to identify vulnerable systems and plan migrations by 2035.
- Layered Security & Hybrid Models: Some blockchains are experimenting with hybrid classical/quantum-resistant signatures, multi-signature wallets where one key is PQC, and re-keying dormant addresses.
- Application and Wallet Best Practices: Developers are encouraged to avoid address reuse, restrict public-key exposure, encourage migrating to quantum-safe wallets, and monitor for post-quantum upgrades.
What’s Changing in 2025
In 2025, the urgency and strategic attention around quantum-blockchain convergence are growing:
- Threat timelines are being revised downward; some estimates now suggest quantum-relevant threats could surface as early as 2026–2027, a tightening from earlier 2030+ projections.
- Crypto funds, exchanges, and infrastructure providers are beginning to issue public statements and risk disclosures that reference quantum computing as a material risk.
- More blockchains are publicly discussing support for PQC upgrades or optional features for quantum-safe accounts.
- Standardization efforts (e.g., NIST PQC and blockchain PQC working groups) are advancing more quickly, and some chains are piloting PQC features.
- Migration complexity is now a key focus: migrating billions of addresses without disrupting network continuity, ensuring inactive wallets don’t become attack surfaces, and upgrading legacy systems.
Conclusion
Quantum computing presents both a profound threat and an opportunity for blockchain networks. While the technology is not yet at a stage to break most live networks, the pace of quantum-hardware progression, the “store now, decrypt later” dynamic, and the sheer scale of value locked in blockchains mean that preparation is no longer optional — it’s critical.
The migration to quantum-resistant cryptography, hybrid signature schemes, and upgradeable infrastructure will define the resilience of blockchains over the next decade. For builders and users alike, the time to act is now.
Build Quantum-Safe Frameworks with Bitium!
At Bitium Web3 Development Agency, we specialise in helping projects audit quantum vulnerability, design PQC-compatible architectures, and build migration roadmaps that ensure security, continuity, and decentralisation remain intact as the quantum era arrives.
Listen To The Article

Black Friday 30%
Offer












